
Threat Landscape Report - The 10 Years Edition
In 2011 two things happened: CERT-EU was born and RSA, a renowned cybersecurity vendor, was hacked.
If history is a great teacher, then we should definitely look back at the major cyber events that
made the headlines in the ten years since 2011, since we were created ...
- Home
- Publications
- Threat Landscape Report - The 10 Years Edition
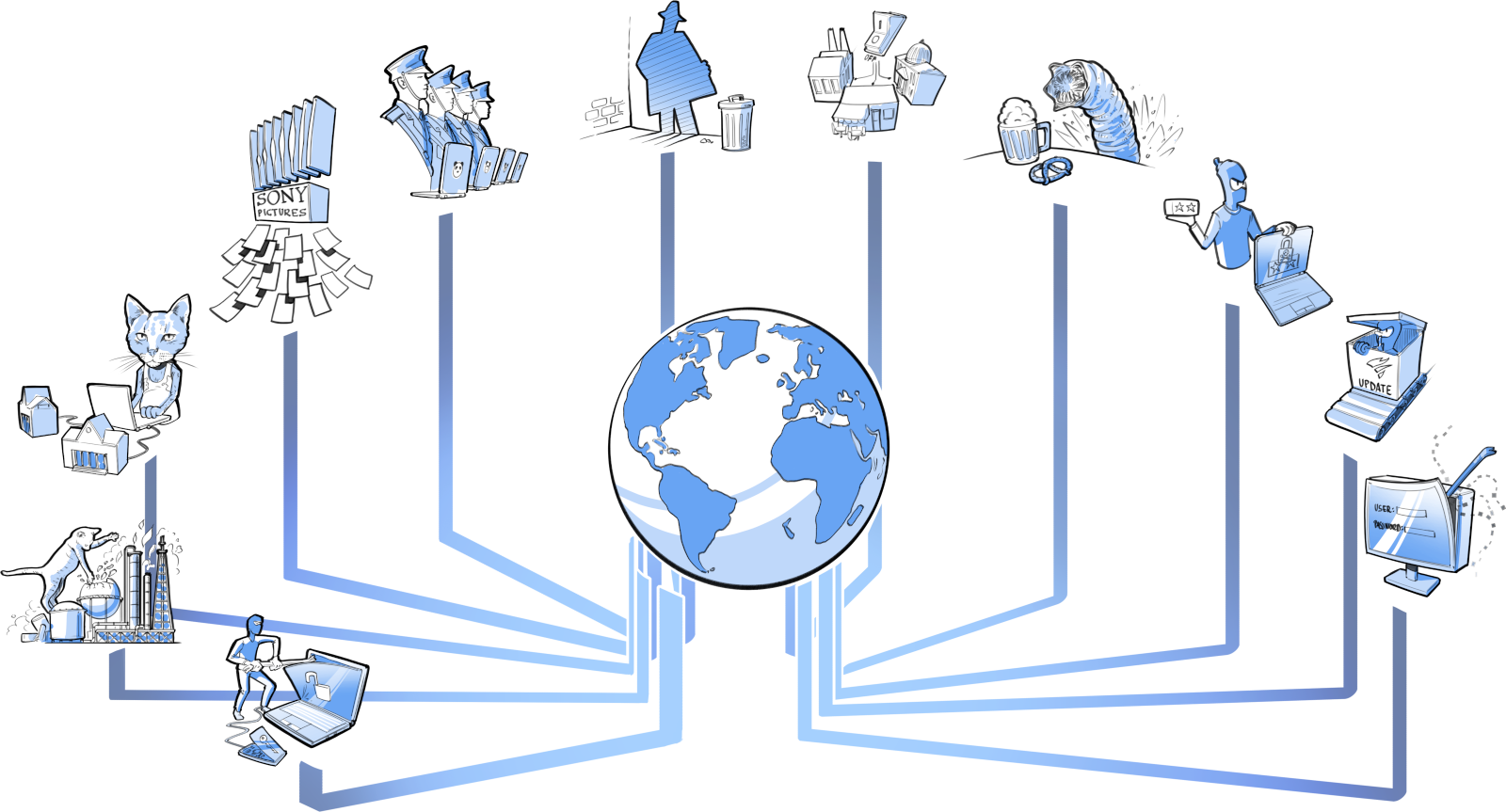
2011
RSA hacked
2012
Shamoon
2013
Iran's Mabna
Institute targets
universities
2014
Sony Pictures
hacked
2015
China's military
cyber forces
established
2016
The Shadow Brokers
2017
WannaCry
2018
Sandworm
2019
Ransomware
double extortion
2020
SolarWinds
by APT29
2021
Log4Shell
2011

Lockheed Martin
hacked via RSA

Blackhole exploit kit

Gmail accounts of
US politicians hacked
Belgacom
hack

IMF compromise

Backdoored
Chinese
equipment


2012

China Chopper

Flame

Shamoon


2013
Red October

CryptoLocker,
the pioneer

Iran’s Mabna
Institute begins
targeting universities
Ke3chang launches
a major campaign


2014

Gamma Group
hacked

Evil Corp emerges

Dridex banking
trojan emerges

Syrian Electronic
Army surfaces
Korea Hydro hacked

Sony Pictures hacked,
films and data leaked


2015

Hacking Team hacked

China-US no-hack agreement

Ukraine’s power grid targeted

China’s military
cyber forces
established


2016

Bangladesh Bank
SWIFT money heist
United Cyber Caliphate created

Tainted leaks
and Guccifer

The Shadow Brokers
The Mirai IoT botnet

Cyber Space
Administration
of China issues
a National
Cybersecurity Strategy


2017

WikiLeaks
Vault7
French elections
hack-and-leak

Lazarus stealing money
for North Korea

DoS of Ukraine’s power grid
WannaCry

NotPetya
causes chaos

ShadowPad supply
chain attack

KRACKing the Wi-Fi
Triton targeting
industrial safety systems


2018

ASUS update system
compromised
Spectre and
Meltdown
CPU flaws

APT28 targets embassies

Olympic
Destroyer

China spies on Uyghurs

VPNFilter, APT28,
and football in Kyiv

Sandworm

Lazarus stealing money
for North Korea
Turkish hacktivists

Russia’s APT28
targeting
elections

Ransomware vs
Managed Service
Providers


2019

Disinformation on Facebook

Facebook
“mistakes”

Huawei sidelined in the US

Turla targeting
MS Exchange

Ransomware vs aviation

Ransomware
double extortion
Russian cyber spies
hack Iranian cyber spies
China removing
foreign hardware
The Great Cannon
of China


2020


Undersea optical
cables probed

China vs global
industries

COVID-19
contact
tracing

Bundestag espionage

Zoom woes

US elections
targeted

European IT giants
targeted with
ransomware
European
Medicines
Agency
breach

SolarWinds
by APT29


2021

ProxyLogon

Pulse Secure
VPN breached
APT29 upstream attacks
Colonial Pipeline
ransomware
Kaseya ransomware

T-Mobile
private
data
breach

Ghostwriter campaign

Log4Shell
GoDaddy hosting
compromise
Important disclaimer
The information used to create this special '10 years' threat landscape report is based on public reports. The illustrations in this web page are inspired by those public reports. They do not necessarily reflect our stance. There have been many cyber events in the period 2011-2021. We tried to select those that made the headlines. This selection is by no means exhaustive.
Oops!
Sorry but you need a decent screen to view this page.
Trust us, you wouldn't want to miss all its glory and beauty by viewing it on the tiny screen
of a phone or of a tablet in portrait mode (landscape works though)!
You wouldn't visit a museum if you needed a magnifying glass to view all the paintings, would
you?
We got cookies
We only use cookies that are necessary for the technical functioning of our website. Find out more on here.
